Click for SiteMap
information-technology:2019-data-security
change site colors:
Table of Contents
I started to write about data portability, but I got quagmired by data security. Data security is a prerequisite of data portability, so the following has nothing to do with data portability, as I had hoped.
2019: Data Security
There are security experts who bend over backwards to make their data secure. Maybe they are right in doing so; life is full of risk. But I wonder to what extent you should go about trying to prevent bad things from happening. If you spend all your time in prevention, then you aren't spending your time living. What is practical? If one or three in a million suffer consequences of insecure data, should everyone have to jump through hoops for the sake of security? I don't know what the odds are, or where to draw the line, but I'm certain security experts have a bias towards security.
I want security with the least amount of work from my part. I also want security for others, that prefer to learn the least amount they need to, to be functional and safe.
Local Encryption
If your laptop and phone are password protected, then as long as they aren't on, logged in, and unattended, your data should be secure, right? There is a caveat. Your phone or laptop can be stolen or appropriated. Then the password is only a minor obstacle. The storage vesicle in your device can be connected to a different operating system, and thus any unencrypted data is accessible. This assumes someone knows how or is motivated to do this.
So for security, not only does your device need to be password protected, but your data also has to be encrypted. The downside to encryption is the overhead in system resources. Encryption requires processing power and therefore consumes energy (fuel, battery, electricity). It can also cause data recovery issues in case of system failure. More details, including a comparison of software versus hardware encryption here.
Data on Android and iOS devices are encrypted (Android since Marshmallow, except on devices that are too slow to handle the encryption overhead). On most mobile devices, data is backed up to the cloud, so there is no need for data recovery if the device fails. With a secure screen lock, you should be set.
Data on Windows can be encrypted with the built-in Bitlocker.
Network Security
But wait, that's not all! Your data should also be secure from the networks you connect your device to. Wifi, cellular, bluetooth, etc, can all be points of vulnerability. For this, you rely on engineers to provide safe networking interfaces. For example:
- If you are using a bluetooth keyboard, then what you are typing should be sent encrypted to your device.
- Your web browser should be free of security vulnerabilities.
If you are using a public Wifi, make sure it's not a rogue hotspot. If there is a rogue hotspot, it's there because someone wants to try to hack you. The chances of this happening is like getting into a car accident, but it's still good to have awareness. The SSID of the rogue Wifi could be slightly different than the official one. For example, the capitalization could be different, such as FreeAirportWifi vs FreeairportWifi. StarbucksWifi vs Starbucks_Wifi. You'll see the two SSID's side by side, and usually, there should only be one.
Most of the web is now using HTTPS (SSL) encrypted communication, which for most people makes a VPN unnecessary. The difference between the two, is that HTTPS will only encrypt traffic between your *browser* and a *website*, while VPN will encrypt all traffic between your *computer* and the *internet*. If you are only using a web browser, that's all the traffic. Modern email clients also communicate over secure connections, so that's covered as well.
The truth about VPN:
“Good and Bad Reasons to use a VPN“
”Don't use VPN Services”
Malware Protection
There is also malware protection, such as antiviruses and firewalls. I have covered this in the past, so will make it short here and possibly expand the article in the future.
While it may be controversial, I don't recommend any “security suite”. Using a content blocker such as Ublock Origin is the most practical and sufficient solution. Knowledge is your best defense. The majority of the “security risk” is just you, and security software can only do so much to protect you from yourself. What it can do, is annoy you to death until you don't have the patience to be careful.
Most any security software that is for profit, will want you to be super-aware about the importance of using their product. To the point that installing their software means installing brain-washing self-promotion software. Your valuable time will be wasted with the unnecessary busyness of configuration dialogs and “We are protecting you, we are so great” types of messages.
Update: I found a 2012 article from wired, that hasn't sold out: Is Antivirus Software a Waste of Money?
Find software that is Free and Open Source, and both your experience and your overall safety will be much better.
NSA Protection
Yes, the government is spying on you. Another vulnerability, supplied by funds from the NSA, paid to Intel and AMD, is an always-on chip that can bypass the operating system and control the computer remotely. Intel and AMD deny this capacity. Vendors such as Purism and System76 ship laptops with these chips disabled. The evidence is pretty convincing: https://en.wikipedia.org/wiki/Intel_Management_Engine.
Digital Privacy
Lastly, there is data privacy, for which the going champion is the EFF organization. Being spied on by corporations wanting to know as much as possible about you, may not seem as important as the risk of having your data destroyed or your money stolen. However, in practicing good habits for data privacy, you become more aware about security in general. It's not a necessity, but if you are interested in wearing a tin foil hat, read on. The European Union is taking privacy seriously, having passed the General Data Protection Regulation (GDPR) on May 25th, 2018.
Ublock Origin, the content blocker mentioned above, serves dual purpose for both security and privacy. Most other related software is inferior and superfluous. See: ublock origins vs privacy badger vs disconnect, Reddit.
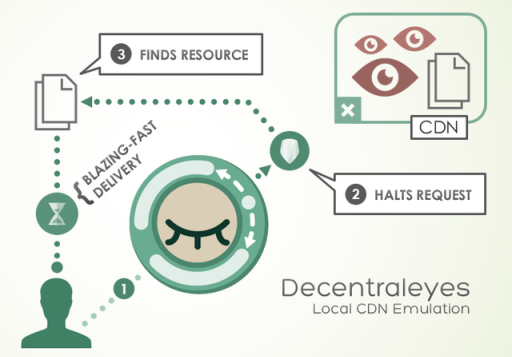
I use two other types of privacy extensions. One to auto delete cookies while I am web browsing (except those I white-list), and another that helps with cookie-less tracking from CDN's (Content Delivery Networks).
Cookie Autodelete for Chrome, or Cookie Exterminator for Pale Moon are easy to operate. Decentraleyes helps with the CDN's, and works transparently. Greedy Cache for Pale Moon Browser works in a similar fashion to speed up web browsing.
I disable all my plugins except flash (set at “never activate”, since “ask to activate” lets a site know you have them available). A combination of plugins and their version numbers can be identifying. When I need a plugin, like in the rare instance I watch Netflix, I will enable the Silverlight plugin.
I tried using an extension called Eclipsed Moon (for Pale Moon Browser), which randomly changes my browser User Agent declaration, so a site thinks I'm on Firefox and Windows 10 for one session, and Chrome and Windows 7 in another session. However, logging into Google, I kept getting security alerts, because “a new device” had connected to my account. This was annoying enough to keep me from continuing to use it.
Instead of constantly changing your user agent, you can use the most common user agent. Since people are constantly updating their web browser, the user agent updates with it. If you are not a fan of updating your system, or you don't use a mainstream web browser, you should use the most common user agent possible. The following are updated lists of the most common user agent:
https://techblog.willshouse.com/2012/01/03/most-common-user-agents
https://github.com/gitbugged/random-agent-spoofer/blob/master/data/json/useragents.json
I don't know why these lists don't agree with the current version of Chrome: https://www.whatismybrowser.com/guides/the-latest-version/chrome
Aside from overcoming these tracking methods, your computer and browser have a sort of digital fingerprint. There are numerous methods to compute a fingerprint, and they can get quite advanced. You can test your browser's ability to be fingerprinted on sites like these:
https://panopticlick.eff.org
https://amiunique.org/fp
https://browserleaks.com
Since I'm using uBlock Origin on medium mode, I passed the panopticlick test, but only because the third party scripts were not able to load. So I'm sort of covered from legal privacy infractions (at least in the European Union). There are numerous tests on browserleaks for which I do not pass.
If the TOR browser has to constantly adapt to keep up with new fingerprinting methods, then I concede futility in trying to find further browser extensions to be incognito. In the same breath, I could add that the TOR browser receives development funding from the government like a military contractor.
Automatically Reject Unnecessary Cookies
“I Don't Care About Cookies” was bought out by Avast/Norton and left to rot (no longer updated). So am looking for a viable option. “I Still Don't Care About Cookies” is a new fork, but it isn't being updated either. uBO (uBlock Origin) has an included filter, but I think it doesn't have code for clicking to dismiss the cookies prompt.
“Consent-O-Matic” seems to be the best replacement.
Deprecated "I don't care about Cookies"
There is one more extension I use, and it's called “I Don't Care About Cookies”. It's an extension that automatically gets rid of cookie warnings on websites, so you don't have to be bothered with dismissing them. It's function is best described in the latest release notes:
“ From this version on, I don't care about cookies browser extension notifies websites about which cookies you allow them to install on your computer.
By default, you allow them to install required cookies, that is, cookies needed for the website to work properly. You don't allow them to install other cookies (in example, cookies related to ads, marketing, analytics…) by default. You can change that in extension's options. Why all this?
Many websites have complicated cookie warnings or don't work properly without accepting the cookie policy. It is even impossible to hide some of those warnings.
By knowing which permission you gave them, websites can skip displaying the cookie warning if they want and act according to the given permission. As a result, you will be bothered by cookie warnings even less then before. ” source
Password Management Strategies
You can search the web for articles about the most frequently used passwords. In my doing so, I found “Today I Am Releasing Ten Million Passwords” by Mark Burnett. I downloaded the usernames and passwords, and checked them against my own. An interesting conclusion, is that 30% of people use passwords that are on the top 10,000 passwords. So a hacker using an automated script can try the most common usernames and passwords first. That 30% of people use passwords on the top 10,000 list, speaks of fatigue. People want convenience.
If you are an avid internet user, you can have dozens if not hundreds of usernames and passwords. People follow different strategies in keeping up with their passwords. They can use
- a password manager
- a password hashing tool
- their memory for a handful of passwords that get used extensively
I suspect the vast majority of people use a handful of passwords, and/or carry around a piece of paper (or an unencrypted text file).
If you use a password management service, it's more secure to use automatically generated passwords. Though you run the risk of being overly reliant on the service.
If you use a password hashing tool, you only need to remember one password, and keep using the same software tool until the end of time. No password is ever stored anywhere. The hashing tool generates a unique password based on the website, your username, and your master password. It would have to be configured to use a set of characters that is most compatible with all websites, otherwise you end up having to keep track of the password policy of each website. The positive is that you don't need to rely on any cloud service.
Alternatively, you could manually hash a password in your mind, thus relying only on your head. This is by far the least complicated way, but if you are ever tortured for your passwords you will likely give them up. If you use a password manager that generates passwords for you, you won't remember your passwords even under excruciating pain.
Password policy can be a royal pain. Password policy means, for example, the requirement that the password contain capitals, special characters, numbers, etc, or that the password be changed on a regular basis. I have yet to figure out a simple way for a password hashing method to cover the requirements from all websites.
Biometrics may be the future, but I'm sure even these could be forged since their representation is stored as data. Current smartphones can use fingerprints and even iris scans. My guess is that the ultimate fate of Biometrics is to serve as a master password, for access to all of your other passwords. However, you can only replace this master key with the number of fingers and iris you have.
Web Browser Stored Passwords
Most people use the password managers built into their web browsers. They are the easiest to use, because no setup is required, and because their auto-fill feature is the most seamless. Most of the time only a single click is required to log in, because the username and password fields are automatically filled in.
If you go into the web browser's settings, you can view all your passwords. For this reason, they are completely insecure and are best combined with disk encryption and a password locked screen (for when you step away from your device).
A Trend Towards Universal Sync of Data Between Devices
If you use Google Chrome on all your devices and sync your profile, this will include syncing your passwords (along with everything, extensions, bookmarks, history, and even payment methods). Firefox, Apple, and Microsoft have also adopted profile sync. For example, with Apple's Continuity, you have features like a universal clipboard and “handoff”, where you can seamlessly continue your work on a document with another device. Information sync is really convenient when you have more than one device.
Manually Importing Passwords Into a Web Browser
If you only use one of the mentioned companies, then this section is not for you. But if you use more than one ecosystem, or you just want to migrate to a different ecosystem, then it may be convenient to be able to migrate passwords between them. There's lots of trouble to be had in the attempt.
It's a problem of data portability. You would think that competing browsers would enable import from other installed browsers on the same system. As far as I know, only Pale Moon Browser has an extension that can import passwords from Chrome, made by a single developer.
On Android, the situation is a little harder. Each application is in its own bubble, such that applications can't access data between each other directly. Maybe that's why Samsung Internet web browser can't import passwords from Chrome. They've invested in Samsung Pass, which allows you to log into applications and websites with an Iris Scan. Yet they won't introduce the convenience of the initial import?
Even on desktop operating systems, web browsers don't have a reliable password import feature. I tried importing into Chrome without success. In Chrome the feature is hidden and experimental. The data fields may not be labelled correctly, or in the same order that the web browser expects. Also, the data for password filling is not just usernames and passwords, but the way in which fields are detected on each website.
On the Lastpass website, regarding passwords imported from other password managers: “Once imported, you might notice that some websites do not autofill right away. This is because LastPass needs to “see” the website in order to capture the exact username and password fields, as they differ from website to website. When you visit the website for the first time after importing, use the field icons to force fill the credentials and login. It will autofill every time after that”.
Password Management Services
The Google, Microsoft, Apple, and even Firefox ecosystems are what most people will use. The following services give you the benefit of being able to sync not only between different operating systems, but also between different web browsers. They are mainly for niche users that want full independence.
I prefer FOSS (Free Open Source Software) and Data Portability. In looking for these in a password management service, I came across Bitwarden as a possible solution. I found a helpful post describing the situation, written by m_a_t_o:
“ While Bitwarden is open source software, its usage is quite restricted. Everything is tied to their online / cloud account. Even if you configure your own server (and it is not light on resources by no means) you need licenses to use some features. Features that are bundled with some other password managers “for free”. Bitwarden desktop apps are really just web apps (Electron framework based), thus heavy on resources and potentially less secure than small native well written apps. Bitwarden underwent security audit but so did many other services / software, e.g. 1Password, Enpass, etc.
So for instance Enpass is not fully open source, but they use open source encrypted database (SQLCipher) and everything is stored locally, no need for internet at all. Enpass does support synchronisation, but not via their servers, rather many 3rd party services or your own (WebDAV or local folder). So you could sync locally via a shared folder. And yes, I do consider it a big advantage that you have complete control where your data is stored. You own your data, don't have to pay at all (for desktop apps) or just one time (for mobile apps), and all features are available to everyone.
Bitwarden is surely not the solution we all would like it to be. If anything I'd rather stick with KeyPass (many implementations). ”
The following are videos to compare the actual usage of different password services, mainly on Android, but also also Windows. Android Oreo made it a more seamless task (?) by introducing the Autofill Service API:
Keepass2Android
Keepass sync setup using Google Drive
Samsung Pass
BitWarden on Android
BitWarden on Windows
Dashlane on Android
Lastpass on Android
I've tried out several password managers, but I settled on Keepass family, which includes a hodge-podge of compatible software developed by different parties:
Keepass, Keepasshtml, PassIFox, and Keepass2Android
Keepass and Keepass2Android sync with each other over NextCloud (which I added on my web hosting server) instead of Google Drive shown in the video above.
I use version 2.38 of Keepass, as it is the last version that will automatically save when Keepasshtml updates a password. Auto-save is done by using a “trigger”. Set up a trigger as follows:
- trigger: user interface changes
- condition: database has unsaved changes
- action: save current database
As I mentioned earlier, the most seamless is the browser's own autofill. Keepasshttp+Passifox make use of the browser's autofill infrastructure. On Kiwi web browser, I don't have this, so I will use Keepass2Android to gradually populate the browser's own autofill as I log into sites I use. If only I could import into the browser directly, this wouldn't be necessary.
Samsung pass automatically logs you in when it sees the username and password fields. I actually don't prefer this, as it may interrupt what I'm currently reading. There was no setting to disable this in Samsung Pass. The auto-fill feature of most web browsers suits me, in that it waits for me to click to log in.
Dashlane says it only works with certain web browsers, but to my surprise, all of Dashlane, Lastpass, and Keepass2Android have been working with Kiwi (Update: Keepass2Android isn't working now, on any browser, and I'm not sure why. Now I doubt what I wrote before.). Dashlane has the most elegant interface, and Lastpass can be annoying if you are near a login but don't want to log in. Dashlane has a Password Changer feature that I hope will work as promised, along with their export feature.
More about setting up on Android here.
information-technology/2019-data-security.txt · Last modified: 2024/08/25 21:16 by marcos
Except where otherwise noted, content on this wiki is licensed under the following license: CC Attribution-Share Alike 4.0 International


Discussion